Sharing this awesome project I ran across today:
https://github.com/bbenchoff/MacSSL#a-port-of-mbed-tls-for-the-classic-macintosh-os-789

 github.com
github.com
https://github.com/bbenchoff/MacSSL#a-port-of-mbed-tls-for-the-classic-macintosh-os-789
MacSSL - A port of Mbed-TLS for the Classic Macintosh OS 7/8/9
This is a C89/C90 port of MbedTLS for Mac System 7/8/9. It works, and compiles under Metrowerks Codewarrior Pro 4. Here's the proof:
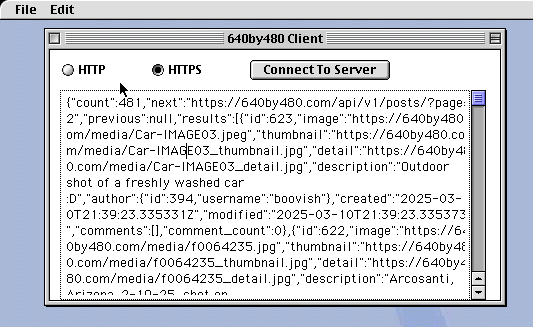
This is a basic app that performs a GET request on whatever is in api.h, and prints the result out to the text box (with a lot of debug information, of course). The idea of this project was to build an 'app' of sorts for 640by480, my 'instagram clone for vintage digital cameras'. The idea would be to login, post images, view images, and read comments. I would need HTTPS for that, so here we are: a port of MbedTLS for the classic mac.
GitHub - bbenchoff/MacSSL: A port of Mbed-TLS for the Classic Macintosh OS 7/8/9
A port of Mbed-TLS for the Classic Macintosh OS 7/8/9 - bbenchoff/MacSSL
